Episode Transcript
[00:00:00] Out of Cycle Update.
[00:00:03] No, not Cybill Shepherd. CryptoTalk FM. My name is Leister. I'm your host.
[00:00:08] An out of Cycle Update for something brought to attention that I thought was fascinating and I felt I would share it with you.
[00:00:16] I'm not going to share the subject matter because unfortunately there's a coward who has precluded doing so. It's fine because we can use some of the supplementary information for educational purposes, which is what we do.
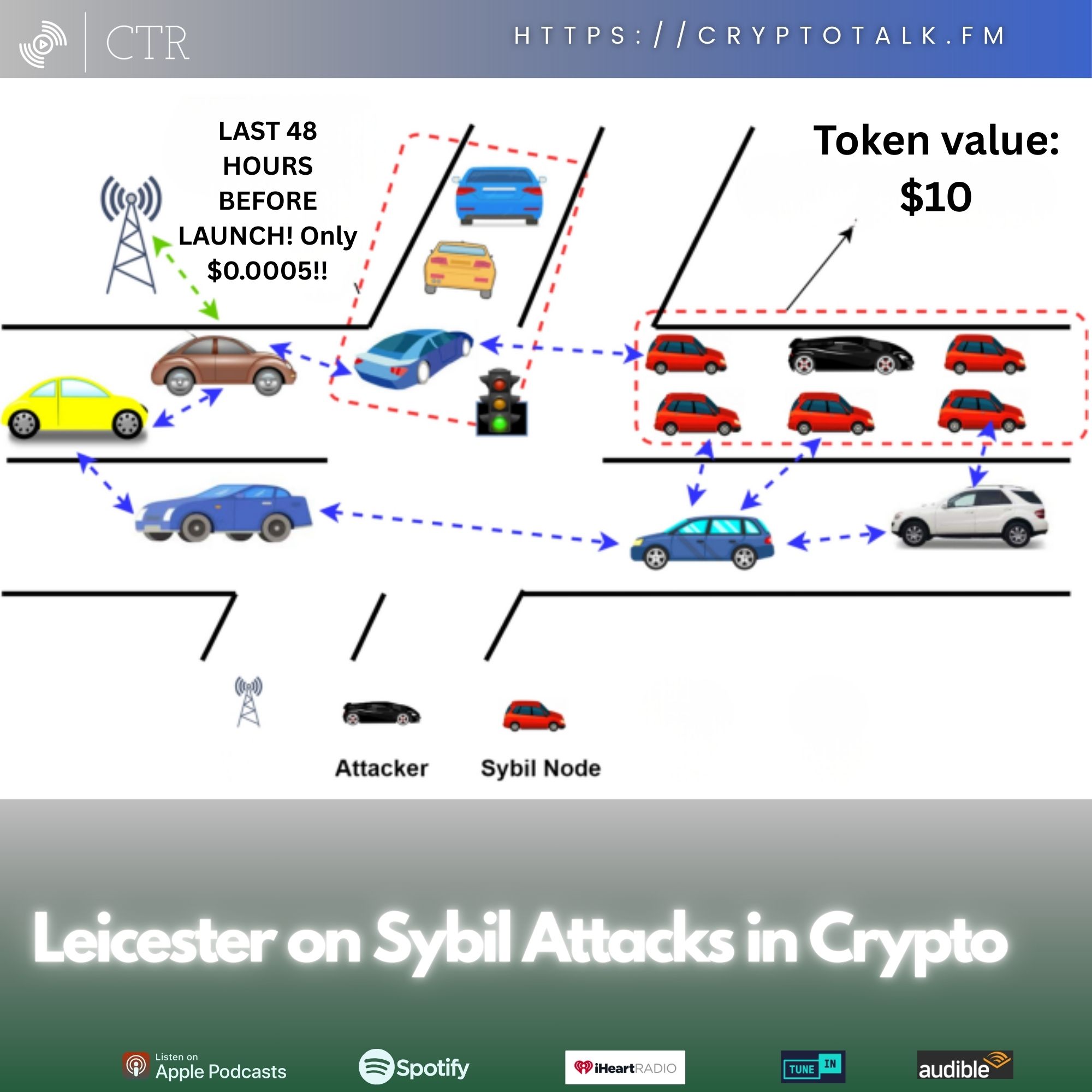
[00:00:33] A Sybil attack. S Y B I L attack.
[00:00:38] What is a Sybil Attack?
[00:00:41] I thought it was good for you to hear from a different lens and an attempt to simplify and just to caveat for some that don't seem to understand this, this is an interpretation.
[00:00:54] People are encouraged to go and research it themselves, create their own interpretation for their own reasons.
[00:01:00] Meanwhile, I can make my own interpretation. It is incumbent look it up on people to do their own interpretation. That's the whole point.
[00:01:09] You should never blindly follow a single person as gospel because then you get into a culture.
[00:01:18] Now, having said that, a Sybil attack at a high level, in order to define it in a way you understand, I have to simplify what leads to it.
[00:01:32] Everybody, I think, understands the concept of a blockchain. It is a ledger. It is an accounting of transactions over time.
[00:01:42] The accounting of transactions has to be maintained.
[00:01:46] The maintenance of the ledger is so that the integrity of the chain is persistent. Look it up.
[00:01:54] We have to make sure that there's acknowledgement of each transaction. So when you go in your wallet and you sign or something, you approve something, you are telling the chain, Yes, I am saying that this is my transaction. Yes, I'm authorizing to do this transaction. Whether that's connected to an application, whether it's sending crypto to somebody, whether it's receiving it.
[00:02:20] Unless the receive is an asynchronous, which is a different thing I won't get into here.
[00:02:25] Point is that there's that first acknowledgement you are acknowledging. I'm making a transaction, I want to commit it up. When your transaction goes up, we'll talk about proof of work because I think it's easier to for people to understand it.
[00:02:37] When you put your transaction up there. There are a whole set of miners M I N E R S out there and they're looking for blocks to work. And as part of the working of blocks, they are rewarded in whichever token. Say Bitcoin. Sure.
[00:02:56] Inside the block are a number of transactions, yours included, that all get then processed.
[00:03:06] Usually there's acknowledgments so there's one person finds it, they process it and say this is a transaction that I'm committing.
[00:03:14] Then ultimately multiple are also finding the same. And then there's computations and calculations that occur in order to do what's being asked.
[00:03:24] And then there's precision and other things we will not get into here. Suffice to say there's a consensus that generally goes along with this that I'm describing to you, which that purpose is to ensure the integrity of the transaction prior to it being fully committed on the chain. This is why sometimes you'll do a transaction and it'll say, like say if you're buying something online or using cryptocurrency and you send it, it'll say we're waiting for this many confirmations.
[00:03:56] That's how many times somebody one of these have checked in to say it's good, it's good, da da da. And they'll ask for like 2 or 3 or something, sometimes up to like 10 or 20, but usually it's like 2 or 3 just to check in to make sure that it's really committed and it's not gonna get rolled back, which is rare. But could that process, once it's done, then they're saying there's an acknowledgement that it's been recognized on chain. We see that it's recognized on chain, we're good to go with it. Now we're okay sending you the whatever currency or whatever product they have their own acknowledgment, let's say it's a crypto that they're sending you. They have an acknowledgement that they gotta wait through when they send it. It's usually pretty quick because it's outbound, but they have an acknowledgment and that shows up in your wallet and then you're done. And then yours. If you were to look at that transaction hash, you'll see on the actual scan you'll see that there's a number of confirmations that keeps happening. So it just keeps happening over time. And this all goes to the integrity of the process in certain of these to make all this happen, to actually create the so called network, to enable everything I just described, you have nodes.
[00:05:10] The nodes are the heart and soul of what make the thing run simple form. And there's always multiple of them.
[00:05:19] Part of the problem I would argue with nodes is, and this lends to the Sybil attack part of the problem and the flaw with nodes is the assumption that everybody has the best of intentions.
[00:05:34] As with any Network.
[00:05:35] If your underlying servers, your routers, your computers, if you have a malicious actor powering this thing, it affects the network and drops its security and creates vulnerabilities.
[00:05:50] Now, with something like blockchain, it's not like it could infect your computer or any of that, because it's not running locally on your device, generally speaking.
[00:06:00] But what it could do is it could compromise the value of your assets.
[00:06:04] If you connect your, your wallet to a D app that's been compromised or that is attached to a node that is compromised or is attached itself to the chain, but the chain has been compromised at a point, then your assets could be drained. So depending on where that compromise is happening, your wallet could be affected. You, the physical, you would not be, but your assets, your stored assets could be.
[00:06:32] Recently I talked about monero and the 51% attack.
[00:06:37] The 51% attack is a type of civil attack. It simply means that an opera, a node operator, is able to control at least 51% or more of the entirety of the network. And when that happens, it allows them to essentially control what's going on. Now, in that case, they weren't doing it for malicious reasons. They were doing it to use the value of Monero to enrich their own token product. And they chimed to Monero and said, we're just showing you we can do this because you're compromised, right?
[00:07:12] Kind of like an ethical hacker. But they were trying to enrich themselves at the same time because it allowed them to influence the price of Monero by doing that.
[00:07:21] So that's a form of civil attack that's easy to understand.
[00:07:24] How many node operators do single actors control?
[00:07:29] Or you have a bunch of malicious actors in collusion with each other to do the same influence. This is the same negative impact.
[00:07:39] Now, if you think about what I just said, there a number of different malicious actors running nodes. Let's make up a scenario. And again, any sort of similarity or connection to real world events or entities is purely speculative and not real. Right? But let's make up some scenarios. Let's say you have an entity formed as an LLC that creates a dao, and I'll pick a United States at random, let's say Wyoming. Right? And they create, or they plan to create node, at least one node. If they're going to run nodes and you have another entity, let's say it's formed in, I don't know, I'll pick a random country. Now, at this point, right? South Africa, you know, or Dubai, or one of these random countries. Let's Just assume you have a world where node operators in these different areas of random kinds are in collusion.
[00:08:32] And the collusion is to make sure that the value of said token for said chain is controlled.
[00:08:43] Depending on how diverse that gets, it could create essentially a liquidity drain on the back end.
[00:08:52] Whether or not they have access to the wallets directly, whether or not they have access to. They could say lock liquidity, they could do all those things that you see. But because they control, ultimately control the network and because they're in collusion, they're working together, they're controlling and directing the route pass, they're controlling and directing the oracles for price discovery, they're controlling everything that makes the thing valuable or not.
[00:09:19] Because of that, it would enable those bad actors, if they exist, to essentially drain the project without you really realizing that that's happened. Unless somebody had enough inside information to see that that's happening. Now how would somebody have that information? Let's take a random one wild eyed scenario. Let's say that you had. Let's say that Dao, right, happened to be led by people who happened to be in direct contact with the CEO, getting information from the CEO or maybe another different random situation, maybe that Dao was in communication with the HR person or a community person, somebody who was inside, right? They're talking to insiders. What if that exchange of information enabled that route, where it enabled them to get access to information not because they were trying to do it, but they were given that information and it gave them the idea to then overtake the vast majority of nodes so that they could initiate a 51% attack. Because in their minds they're trying to protect the chain, they're trying to protect people, they're trying to keep people safe, they're trying to. They got the best of intentions, they're vigilantes, right? So that Dow again, and I picked a random state of Wyoming, but it could be any state. But that Dow, let's say they set up enough nodes to be able to execute a 51% attack because they're thinking, they're trying to control, because they're trying to prevent somebody else whose nodes are in say South Africa or Dubai from doing it.
[00:11:02] That sounds like a battleground, doesn't it? Like a, like an army, right? And you have highest ranking officers on one side and you got this guy and he's like as general of my hands up, right? I'm not a man, you know, it's something to think about. But the point is that the civil attack can impact Any project where there is no we have some form of transparency in terms of who's all the players at the front of it.
[00:11:31] I don't know that there's full transparency in any of them. With the node level, I don't know if that's really fully clear. Some are, but not all. And even the ones where it is somewhat you still end up having 51% attacks happen. Ethereum Classic was a great example.
[00:11:47] My point is that it can happen to any chain.
[00:11:51] Most chains that did happen to did recovery.
[00:11:54] So there's light at the end of the tunnel if it is subject to such an attack.
[00:11:58] But it's important for you to understand the, the importance of how complex these kinds of tricks are. Now, it's not as simple as like Saitama owner sitting on the wallet of full liquidity and they could just drain it because that's too easy, right? They're, they're doing things behind the scenes that can drain it without having to have that front end spotlight on the ability to drain it. So when you're trying to assess a project as I close, sometimes you're not going to know up front. Sometimes you're not going to be aware that that risk is there. Especially if the audit was not transparent or not complete or not done against prod production.
[00:12:40] And sometimes the audits can't catch it because usually that kind of node diversity develops over time. So up front it might be clean, but then over time you're building out all these nodes and if there's not a transparent identification and identity and KYC process in front of it, you don't know what those people are doing. Even if you do identify them. If certain people are good at tricking you into thinking that they're on your side, let's say, hey, I'm here to support the chain and I'm here to represent you. They're saying that up front, but behind the scenes in secret. They're in collusion with the leadership of the project.
[00:13:19] How do you know that they're they have your best interest at heart by doing so. If they're not transparently talking about things that are to your detriment that they were aware of. That's what happened with the ship ecosystem and certain others. So that's my feedback to you is consider sometimes you're not going to know going in. You're not going to know that this malicious activity begins to happen post launch. Sometimes a project can launch and it's fine, and then after launch this happens. That's what then causes the pump and dump graph that you often see on projects.